<xs:complexType name="Attack_PatternType">
<xs:sequence>
<xs:element name="Description" minOccurs="0">
<xs:annotation>
<xs:documentation>This field contains a detailed description of the attack including the chain of actions taken by the attacker. More comprehensive descriptions could include relevant attack trees and/or exploit graphs to more clearly elaborate this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Summary" type="capec:Structured_Text_Type">
<xs:annotation>
<xs:documentation>Brief description of what the attack involves and what weaknesses it is leveraging for exploit.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element ref="capec:Attack_Execution_Flow" minOccurs="0">
<xs:annotation>
<xs:documentation>Outline of the steps involved in an attacker executing the typical flow of the attack.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element ref="capec:Alternate_Terms" minOccurs="0">
<xs:annotation>
<xs:documentation>This element contains one or more Alternate_Term elements, each ofwhich contains other names used to describe this attack pattern.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Target_Attack_Surface" type="capec:Target_Attack_SurfaceType" minOccurs="0"/>
<xs:element name="Attack_Prerequisites" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the conditions that must exist or the functionality and characteristics that the target software must have or behavior it must exhibit for an attack of this type to succeed.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Attack_Prerequisite" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual attack prerequisite.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Typical_Severity" minOccurs="0">
<xs:annotation>
<xs:documentation>On a rough scale (Very Low, Low, Medium, High, Very high), what is the typical severity of impact to the targeted software if this attack occurs? The severity of a specific attack instance can vary greatly depending on the specific context of the target software under attack. This field is intended to capture an overall typical average value for this type of attack with the understanding that it will not be completely accurate for all attacks.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Very High"/>
<xs:enumeration value="High"/>
<xs:enumeration value="Medium"/>
<xs:enumeration value="Low"/>
<xs:enumeration value="Very Low"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
<xs:element name="Typical_Likelihood_of_Exploit" minOccurs="0">
<xs:annotation>
<xs:documentation>On a rough scale (Very Low, Low Medium, High, Very High), what is the overall likelihood of this type of attack typically succeeding considering the attack prerequisites, targeted weakness attack surface, skill required and resources required as well as available and likely implemented blocking solutions? The likelihood of exploit of a specific attack instance can vary greatly depending on the specific context of the target software under attack. This field is intended to capture an overall typical average value for this type of attack with the understanding that it will not be completely accurate for all attacks.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Likelihood" type="xs:string" minOccurs="0">
<xs:annotation>
<xs:documentation>On a rough scale (Very Low, Low Medium, High, Very High), what is the overall likelihood of this type of attack typically succeeding considering the attack prerequisites, targeted weakness attack surface, skill required and resources required as well as available and likely implemented blocking solutions?</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Explanation" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field captures any useful explanation for the defined Likelihood.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Methods_of_Attack" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the mechanism of attack used by this pattern. This field can help define the applicable attack surface required for this attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Method_of_Attack" minOccurs="0" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes the mechanism of attack used by this pattern. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined vectors which is currently incomplete and will grow as new relevant vectors are identified. This field can help define the applicable attack surface required for this attack.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Injection"/>
<xs:enumeration value="Modification of Resources"/>
<xs:enumeration value="Protocol Manipulation"/>
<xs:enumeration value="Analysis"/>
<xs:enumeration value="API Abuse"/>
<xs:enumeration value="Brute Force"/>
<xs:enumeration value="Flooding"/>
<xs:enumeration value="Time and State"/>
<xs:enumeration value="Spoofing"/>
<xs:enumeration value="Social Engineering"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Examples-Instances" minOccurs="0">
<xs:annotation>
<xs:documentation>This field contains explanatory examples or demonstrative exploit instances of this attack, which are intended to help the reader understand the nature, context and variability of the attack in more practical and concrete terms.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Example-Instance" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual example or exploit instance.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Example-Instance_Description" type="capec:Structured_Text_Type">
<xs:annotation>
<xs:documentation>This field describes in detail a specific example or exploit instance of this attack. It should outline the context of the attack, the targeted software, the targeted weaknesses or vulnerabilities, the specific set of actions involved in the attack and the resulting impact of the attacks success or failure (in the case of counterexamples).</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="References" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element name="Reference" type="capec:Reference_Type" maxOccurs="unbounded"/>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Example-Instance_Related_Vulnerabilities" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element name="Example-Instance_Related_Vulnerability" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field lists the specific vulnerabilities targeted by this exploit instance of the attack. Specific vulnerabilities should reference industry-standard identifiers such as Common Vulnerabilities and Exposures (CVE) numbers and/or US-CERT numbers.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Attacker_Skills_or_Knowledge_Required" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the level of skills or specific knowledge required by an attacker to execute this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Attacker_Skill_or_Knowledge_Required" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes the level of skill or specific knowledge required by an attacker to execute this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Skill_or_Knowledge_Level" minOccurs="0">
<xs:annotation>
<xs:documentation>This should be communicated on a rough scale (Low, Medium, High). For example: • Low - Basic computer familiarity • Low - Basic SQL knowledge • Medium - Moderate scripting and shell experience and ability to disassemble and decompile • High - Expert knowledge of LINUX kernel • High - Detailed knowledge of target software development practices and business context (former employee) • Etc.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Low"/>
<xs:enumeration value="Medium"/>
<xs:enumeration value="High"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
<xs:element name="Skill_or_Knowledge_Type" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field provides contextual detail for the skill or knowledge level.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Resources_Required" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the resources (CPU cycles, IP addresses, tools, etc.) required by an attacker to effectively execute this type of attack.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Probing_Techniques" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes techniques typically used to probe and reconnoiter a potential target to determine vulnerability and/or to prepare for this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Probing_Technique" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual probing technique.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Description" type="capec:Structured_Text_Type" minOccurs="0"/>
<xs:element name="Observables" type="cybox:ObservablesType" minOccurs="0"/>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Indicators-Warnings_of_Attack" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes activities, events, conditions or behaviors that could serve as indicators that an attack of this type is imminent, in progress or has occurred.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Indicator-Warning_of_Attack" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual indicator/warning.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Description" type="capec:Structured_Text_Type" minOccurs="0"/>
<xs:element name="Observables" type="cybox:ObservablesType" minOccurs="0"/>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Obfuscation_Techniques" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes techniques typically used to disguise the fact that an attack of this type is imminent, in progress or has occurred.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Obfuscation_Technique" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual obfuscation technique.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Description" type="capec:Structured_Text_Type" minOccurs="0"/>
<xs:element name="Observables" type="cybox:ObservablesType" minOccurs="0"/>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Solutions_and_Mitigations" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes actions or approaches that can potentially prevent or mitigate the risk of this attack. These solutions and mitigations are targeted to improve the resistance of the target software and thereby reduce the likelihood of the attack's success or to improve the resilience of the target software and thereby reduce the impact of the attack if it is successful.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Solution_or_Mitigation" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual blocking solution or mitigation.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Attack_Motivation-Consequences" minOccurs="0">
<xs:annotation>
<xs:documentation>What is the attacker trying to achieve by using this attack? This is not the end business/mission goal of the attack within the target context but rather the specific technical result desired that could be leveraged to achieve the end business/mission objective. This information is useful for aligning attack patterns to threat models and for determining which attack patterns are relevant for a given context.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Attack_Motivation-Consequence" type="capec:Common_ConsequenceType" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>What is the attacker trying to achieve by using this attack? This is not the end business/mission goal of the attack within the target context but rather the specific technical result desired that could be leveraged to achieve the end business/mission objective. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined motivations/consequences which is currently incomplete and will grow as new relevant possibilities are identified. This information is useful for aligning attack patterns to threat models and for determining which attack patterns are relevant for a given context.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Injection_Vector" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes, as precisely as possible, the mechanism and format of an input-driven attack of this type. Injection vectors must take into account the grammar of an attack, the syntax accepted by the system, the position of various fields, and the ranges of data that are acceptable.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Payload" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the code, configuration or other data to be executed or otherwise activated as part of an injection-based attack of this type.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Activation_Zone" type="capec:Structured_Text_Type" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the area within the target software that is capable of executing or otherwise activating the payload of an injection-based attack of this type. The activation zone is where the intent of the attacker is put into action. The activation zone may be a command interpreter, some active machine code in a buffer, a client browser, a system API call, etc.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Payload_Activation_Impact" minOccurs="0">
<xs:annotation>
<xs:documentation>This field is a description of the impact that the activation of the attack payload for an injection-based attack of this type would typically have on the confidentiality, integrity or availability of the target software.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Description" type="capec:Structured_Text_Type" minOccurs="0"/>
<xs:element name="Observables" type="cybox:ObservablesType" minOccurs="0"/>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Related_Weaknesses" minOccurs="0">
<xs:annotation>
<xs:documentation>Which specific weaknesses does this attack target and leverage? Specific weaknesses (underlying issues that may cause vulnerabilities) reference the industry-standard Common Weakness Enumeration (CWE). This list should include not only those weaknesses that are directly targeted by the attack but also those whose presence can directly increase the likelihood of the attack succeeding or the impact if it does succeed.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Related_Weakness" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual related weakness.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="CWE_ID" type="xs:integer">
<xs:annotation>
<xs:documentation>The CWE_ID is a field that exists for all weaknesses enumerated in the Common Weakness Enumeration (CWE). It is a unique value that allows each weakness to be unambiguously identified. The CWE_ID field for the attack pattern contains the value of the CWE_ID for the specific related weakness.</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Weakness_Relationship_Type">
<xs:annotation>
<xs:documentation>This field describes the nature of the relationship between this weakness and the attack pattern. Weaknesses that are specifically targeted by the attack are of type "Targeted". Weaknesses which are not specifically targeted but whose presence may increase the likelihood of the attack succeeding or the impact of the attack if it does succeed are of type "Secondary".</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Targeted"/>
<xs:enumeration value="Secondary"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Related_Vulnerabilities" minOccurs="0">
<xs:annotation>
<xs:documentation>What specific vulnerabilities does this attack target and leverage? Specific vulnerabilities should reference industry-standard identifiers such as Common Vulnerabilities and Exposures (CVE ) numbers and/or US-CERT numbers. As vulnerabilities are much more specific and localized than weaknesses, it is typically rare that an attack pattern will target specific vulnerabilities. This would most likely occur if they are targeting vulnerabilities in underlying platforms, frameworks, libraries, etc.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Related_Vulnerability" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual related vulnerability.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Vulnerability_ID" type="xs:string">
<xs:annotation>
<xs:documentation>This field uses the unique reference ID for a specific related vulnerability utilizing an industry standard vulnerability listing (e.g., CVE-2006-4192, VU#650769, etc.).</xs:documentation>
</xs:annotation>
</xs:element>
<xs:element name="Vulnerability_Description" type="capec:Structured_Text_Type">
<xs:annotation>
<xs:documentation>This field contains a short textual description of the specific related vulnerability taken from the industry standard vulnerability listing.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Related_Attack_Patterns" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies other attack patterns that are somehow related to, dependent on, typically chained together, etc. with this pattern.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Related_Attack_Pattern" type="capec:RelationshipType" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual related attack pattern.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Relevant_Security_Requirements" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies specific security requirements that are relevant to this type of attack and are general enough to offer opportunities for reuse.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Relevant_Security_Requirement" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual relevant security requirement.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Relevant_Design_Patterns" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies specific relevant design patterns that are recommended as providing resistance or resilience to this attack, or which are not recommended as they are particularly susceptible to this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Recommended_Design_Patterns">
<xs:complexType>
<xs:sequence>
<xs:element name="Recommended_Design_Pattern" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual design pattern that is recommended due to its likelihood of increasing the software's resistance or resiliency to this type of attack.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Non-Recommended_Design_Patterns">
<xs:complexType>
<xs:sequence>
<xs:element name="Non-Recommended_Design_Pattern" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual design pattern that is not recommended due to its likelihood of decreasing the software's resistance or resiliency to this type of attack.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Relevant_Security_Patterns" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies specific security patterns that are recommended as providing resistance or resilience to this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Relevant_Security_Pattern" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual relevant security pattern.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Related_Security_Principles" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies specific security principles relevant to this attack pattern. The security principles that this field references come from the set available on the Build Security In website.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Related_Security_Principle" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual security principle.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Related_Guidelines" minOccurs="0">
<xs:annotation>
<xs:documentation>This field identifies existing security guidelines that are relevant to identifying or mitigating this type of attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Related_Guideline" type="capec:Structured_Text_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes an individual related guideline.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Purposes" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the generalized purposes of the pattern in order to enable the capture of pattern composibility. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined purposes which may be currently incomplete and may grow as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Purpose" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field describes the generalized purpose of the pattern in order to enable the capture of pattern composibility. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined purposes which may be currently incomplete and may grow as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Reconnaissance"/>
<xs:enumeration value="Penetration"/>
<xs:enumeration value="Exploitation"/>
<xs:enumeration value="Obfuscation"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="CIA_Impact" minOccurs="0">
<xs:annotation>
<xs:documentation>This field characterizes the typical relative impact of this pattern on the confidentiality, integrity and availability of the targeted software.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Confidentiality_Impact" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the typical impact of this pattern on the confidentiality characteristics of the targeted software and related data.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Low"/>
<xs:enumeration value="Medium"/>
<xs:enumeration value="High"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
<xs:element name="Integrity_Impact" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the typical impact of this pattern on the integrity characteristics of the targeted software and related data.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Low"/>
<xs:enumeration value="Medium"/>
<xs:enumeration value="High"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
<xs:element name="Availability_Impact" minOccurs="0">
<xs:annotation>
<xs:documentation>This field describes the typical impact of this pattern on the availability characteristics of the targeted software and related data.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Low"/>
<xs:enumeration value="Medium"/>
<xs:enumeration value="High"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Technical_Context" minOccurs="0">
<xs:annotation>
<xs:documentation>This field characterizes the technical context where this pattern is applicable.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Architectural_Paradigms" minOccurs="0">
<xs:annotation>
<xs:documentation>This field outlines the architectural paradigms of target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined paradigms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Architectural_Paradigm" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field outlines the architectural paradigms of target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined paradigms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Mainframe"/>
<xs:enumeration value="Client-Server"/>
<xs:enumeration value="n-Tier"/>
<xs:enumeration value="Web"/>
<xs:enumeration value="SOA"/>
<xs:enumeration value="Other"/>
<xs:enumeration value="All"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Frameworks" minOccurs="0">
<xs:annotation>
<xs:documentation>This field outlines the frameworks used as part of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined frameworks which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Framework" minOccurs="0" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field outlines the frameworks used as part of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined frameworks which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="J2EE"/>
<xs:enumeration value=".NET"/>
<xs:enumeration value="Struts"/>
<xs:enumeration value="Spring"/>
<xs:enumeration value="Hibernate"/>
<xs:enumeration value="Other"/>
<xs:enumeration value="All"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Platforms" minOccurs="0">
<xs:annotation>
<xs:documentation>This field outlines the platforms (OS) of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined platforms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Platform" minOccurs="0" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field outlines the platforms (OS) of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined platforms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Windows"/>
<xs:enumeration value="UNIX-LINUX"/>
<xs:enumeration value="Solaris"/>
<xs:enumeration value="Other"/>
<xs:enumeration value="All"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
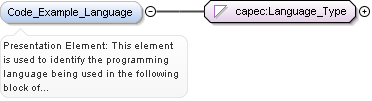
<xs:element name="Languages" minOccurs="0">
<xs:annotation>
<xs:documentation>This field outlines the implementation languages of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined platforms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Language" minOccurs="0" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field outlines the implementation languages of the target software where the pattern is possible and relevant. In order to assist in normalization and classification, this field involves a selection from an enumerated list of defined platforms which may be currently incomplete and may grow or change as new relevant possibilities are identified.</xs:documentation>
</xs:annotation>
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="AJAX"/>
<xs:enumeration value="ASP"/>
<xs:enumeration value="ASP.NET"/>
<xs:enumeration value="C"/>
<xs:enumeration value="C++"/>
<xs:enumeration value="C#"/>
<xs:enumeration value="Java"/>
<xs:enumeration value="JSP"/>
<xs:enumeration value="PHP"/>
<xs:enumeration value="PERL"/>
<xs:enumeration value="Ruby"/>
<xs:enumeration value="Visual Basic"/>
<xs:enumeration value="Other"/>
<xs:enumeration value="All"/>
</xs:restriction>
</xs:simpleType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="Keywords" minOccurs="0">
<xs:annotation>
<xs:documentation>This field is intended to be a catch-all field for assisting in searching and subsecting a collection of patterns according to criteria not contained elsewehre in this schema.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Keyword" type="xs:string" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field contains an individual keyword to be used for tagging and searching.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="References" minOccurs="0">
<xs:annotation>
<xs:documentation>This field enumerates reference resources that were used to develop the definition of this attack pattern and those that could prove valuable to the reader looking for further information on this attack.</xs:documentation>
</xs:annotation>
<xs:complexType>
<xs:sequence>
<xs:element name="Reference" type="capec:Reference_Type" maxOccurs="unbounded">
<xs:annotation>
<xs:documentation>This field should describe the reference clearly and unambiguously by name and with some method of address such that the reader can locate the resource for further reference.</xs:documentation>
</xs:annotation>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element ref="capec:Other_Notes" minOccurs="0"/>
<xs:element ref="capec:Maintenance_Notes" minOccurs="0"/>
<xs:element ref="capec:Content_History" minOccurs="0"/>
</xs:sequence>
<xs:attribute name="ID" type="xs:integer" use="optional" default="0"/>
<xs:attribute name="Name" type="xs:string" use="required"/>
<xs:attribute name="Pattern_Completeness">
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Complete"/>
<xs:enumeration value="Stub"/>
<xs:enumeration value="Hook"/>
</xs:restriction>
</xs:simpleType>
</xs:attribute>
<xs:attribute name="Pattern_Abstraction" use="optional">
<xs:simpleType>
<xs:restriction base="xs:string">
<xs:enumeration value="Meta"/>
<xs:enumeration value="Standard"/>
<xs:enumeration value="Detailed"/>
</xs:restriction>
</xs:simpleType>
</xs:attribute>
<xs:attribute name="Status" type="capec:Status_Type" use="required">
<xs:annotation>
<xs:documentation>The Status attribute defines the status level for this view.</xs:documentation>
</xs:annotation>
</xs:attribute>
</xs:complexType> |